Story
Noun
- Real people and events told for entertainment
- The commercial prospects or circumstances of a particular company

Security Operations Center
Syntory Guardian Angel (SGA) is the name of our comprehensive Security Operations Center (SOC) services that deliver 24/7 security monitoring for your business.
A Security Operations Center is a vital component of an organisation’s cyber security strategy. It is responsible for detecting, analysing, and responding to security threats and incidents in real-time. As cyber threats continue to evolve and become more sophisticated, it has become increasingly critical for organisations to have a SOC to protect against them.
SGA offers three tiers of SOC services to meet your unique security needs:

Post-breach is activated by honeypot traps that we strategically place across your network. If a breach occurs, our SOC experts will be immediately notified and will assist you with the necessary steps to contain and remediate the breach.
Co-SOC combines our AI technology with our 24/7 SOC service. Our experts monitor critical and high priority alerts in real time and respond to them promptly. Meanwhile, your IT team can focus on medium and low priority events, knowing that our SOC experts have their back.

In our Full SOC service our SOC team takes care of all priority levels of events, relieving your IT team of IT security follow-up responsibilities. With SGA Full SOC, you can rest easy knowing that your business is protected by the best SOC experts and technology available.

Cyber Security integrator background

Relieving sysadmins

Short lines of communication & personal guarantee C-level

Partnership with technology partners

Syntory holding – track record in SOC
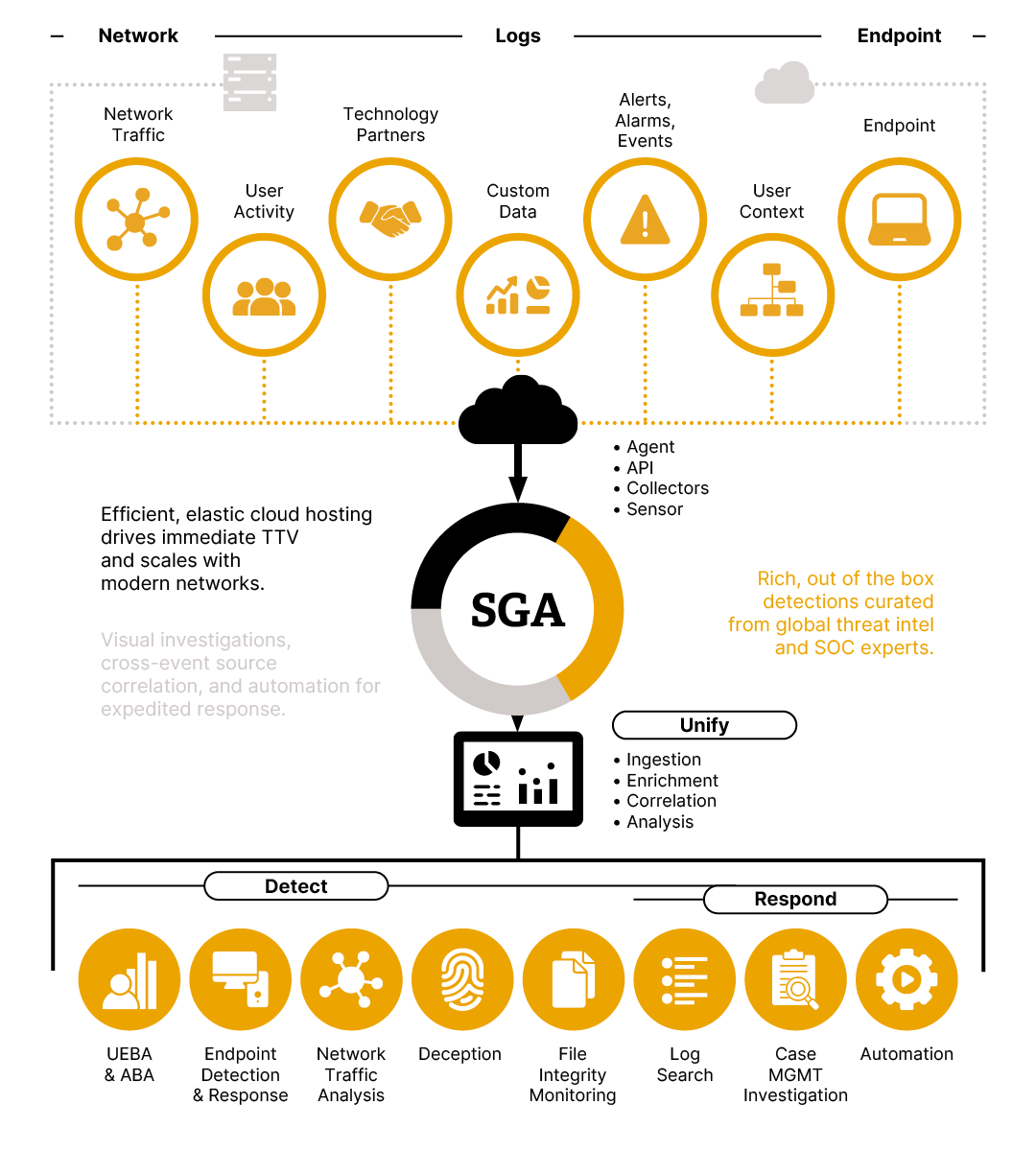
Syntory Guardian Angel is your security center for incident detection and response, authentication monitoring, and endpoint visibility. It identifies unauthorized access from external and internal threats and highlights suspicious activity so you don’t have to weed through thousands of data streams.
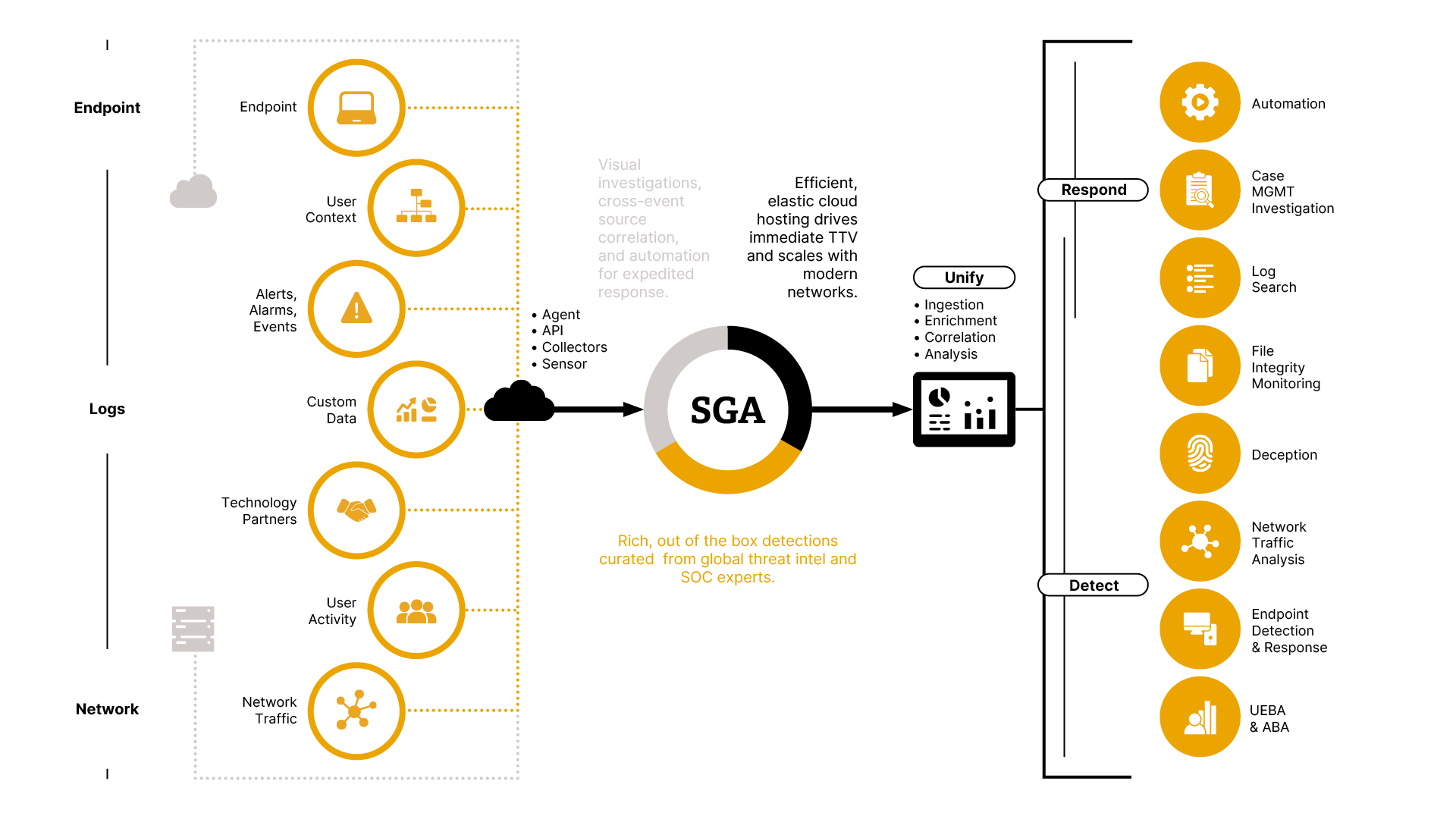
Syntory Guardian Angel is your security center for incident detection and response, authentication monitoring, and endpoint visibility. It identifies unauthorized access from external and internal threats and highlights suspicious activity so you don’t have to weed through thousands of data streams.
Noun
Noun